Sidebar
This is an old revision of the document!
Table of Contents
Spring Security Hello World application
For better understanding how the ADUCID Spring security adapter works and how to configure it, sample application is delivered.
Get sources and binaries on GitHub
The application can be used in any JEE Web containers, supporting Servlet >2.4 specification. The application is available at [[http://your_server/aducid-spring-security-webapp/ (we recommend remove version number from archive name before deployment).
It has following structure:
Root
-> META-INF
-> spring
-> applicationContext.xml (holding spring security configuration)
-> webmvc-config.xml (holding spring mvc configuration)
-> WEB-INF
-> pages
-> index.jsp (main page)
-> identity.jsp (cyber identity attributes)
-> user.jsp (user attribute set and roles)
-> admin.jsp (admin page secured by role admin)
-> error.jsp (error page)
-> lib (additional libraries)
-> classes (classes and property files)
-> web.xml (web application descriptor)
Main page
Main page contains links to other pages with examples. The Logout link clears current authentication session and allows log in again.
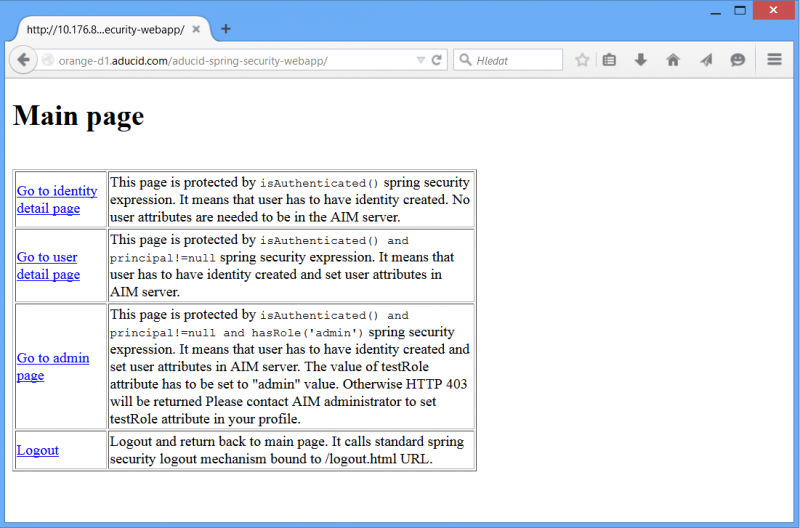
Identity page
Identity page shows example how to get cyber identity attributes, when you have logged in with ADUCID. It contains jstl + scriptlets to get these information from authenticated AducidAuthenticationToken object stored in SecurityContextHolder.
To access this page at least cyber identity has to be created (it is not necessary to create user attributes-user profile).
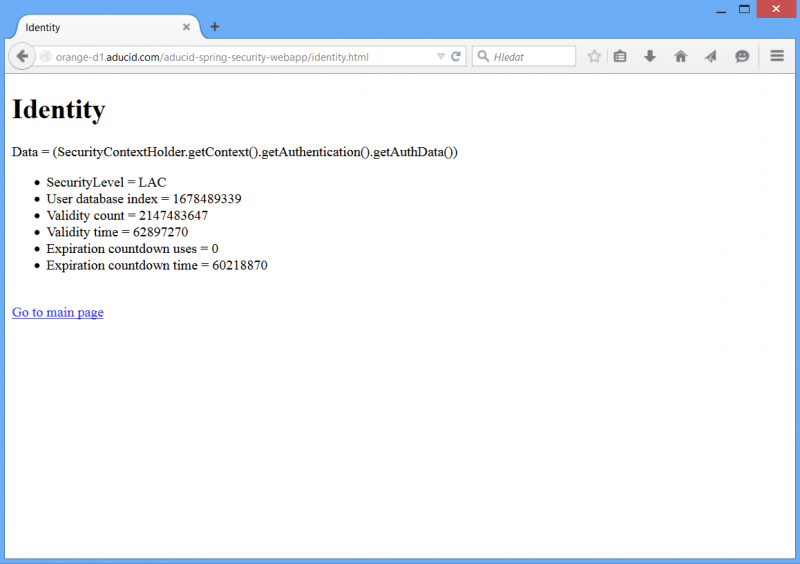
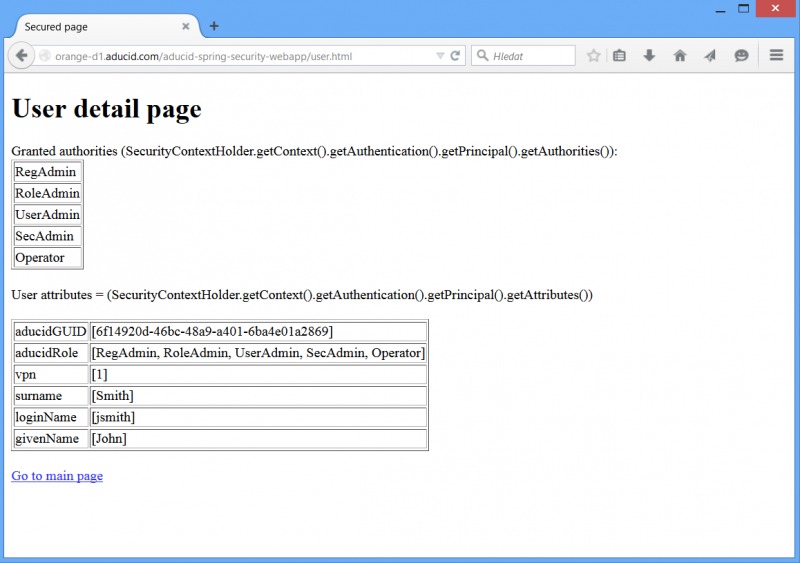
User detail page
User detail page shows example how to access user attributes tied to cyber identity. It contains jstl + scriptlets to get these information from authenticated AducidAuthenticationToken object stored in SecurityContextHolder.
To access this page at least cyber identity and user attributes has to be created. When these conditions are not sufficed, http 403 is thrown back. It is not necessary to have role assigned to the user.
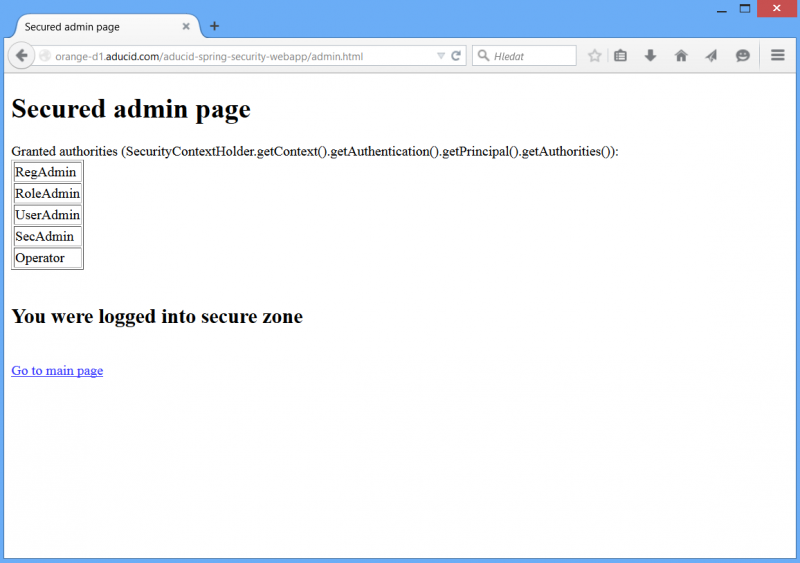
Secured admin page
Secured admin page is the example of how the role based authorization works. The security constraint is configured in applicationContext.xml using spring security el language, more detail hasRole(‚UserAdmin‘) construct is used.
To access this page cyber identity, user attributes has to be created and attribute aducidRole has to be filled by role manager application. Here value “UserAdmin” is expected. When these conditions are not sufficed, http 403 is thrown back.
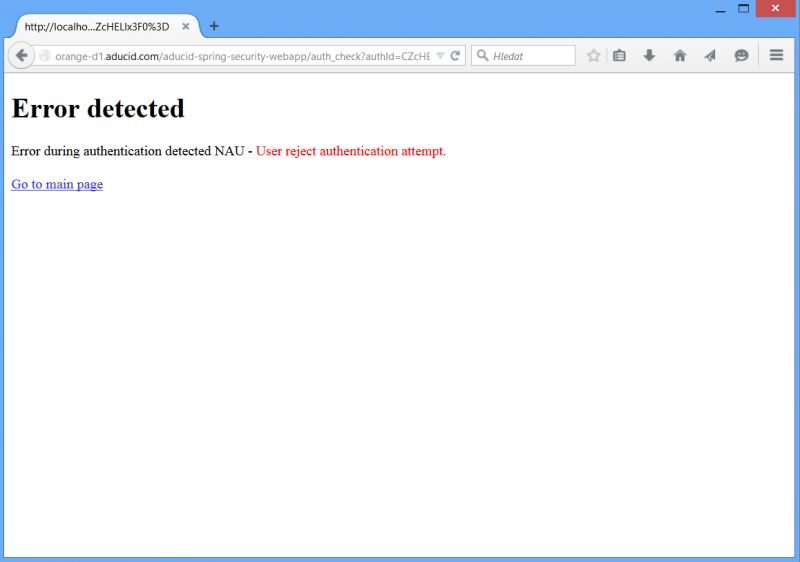
Error page
Error page is displayed whenever any exception is thrown during authentication process. Two ADUCID specific exceptions can be thrown away.
- AducidAutheticationException – the general one that means something unspecified happened
- AducidStatusException - this exception holds status of the authentication process in attributes AIMStatus and AuthStatus. Based on these two statuses, more specific actions can be taken in the application.
Appendix A
This appendix contains complete sample xml configuration of ADUCID spring security adapter.
<?xml version="1.0" encoding="UTF-8"?>
<beans:beans xmlns="http://www.springframework.org/schema/security"
xmlns:beans="http://www.springframework.org/schema/beans" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xmlns:util="http://www.springframework.org/schema/util"
xsi:schemaLocation="http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd
http://www.springframework.org/schema/security http://www.springframework.org/schema/security/spring-security.xsd
http://www.springframework.org/schema/util http://www.springframework.org/schema/util/spring-util.xsd">
<!-- HTTP security configurations -->
<http entry-point-ref="aducidEntryPoint" auto-config="true"
use-expressions="true">
<custom-filter before="CAS_FILTER" ref="aducidFilter" />
<logout logout-url="/logout.html" logout-success-url="/" />
<intercept-url pattern="/identity.html" access="isAuthenticated()" />
<intercept-url pattern="/user.html" access="isAuthenticated() and principal!=null" />
<intercept-url pattern="/admin.html" access="isAuthenticated() and hasRole('UserAdmin')" />
</http>
<util:properties id="aducidProperties">
<beans:prop key="aimUrl">http://localhost:8080/AIM</beans:prop>
<beans:prop key="aimProxyUrl">http://localhost:8080/AIM-proxy</beans:prop>
</util:properties>
<beans:bean
class="org.springframework.beans.factory.config.PropertyPlaceholderConfigurer">
<beans:property name="properties" ref="aducidProperties"/>
</beans:bean>
<authentication-manager alias="aducidAuthenticationManager">
<authentication-provider ref="aducidAuthenticationProvider" />
</authentication-manager>
<beans:bean id="aducidEntryPoint"
class="com.aducid.spring.security.AducidAuthenticationEntryPoint">
<beans:property name="aimUrl" value="${aimUrl}/services/R4" />
<beans:property name="defaultLoginUrl" value="${aimProxyUrl}/process" /> </beans:bean>
<beans:bean id="aducidFilter"
class="com.aducid.spring.security.AducidAuthenticationFilter">
<beans:property name="authenticationManager" ref="aducidAuthenticationManager" />
<beans:property name="authenticationFailureHandler">
<beans:bean id="aducidAuthenticationFailureHandler"
class="org.springframework.security.web.authentication.SimpleUrlAuthenticationFailureHandler">
<beans:property name="defaultFailureUrl" value="/error.html" />
<beans:property name="useForward" value="true" />
</beans:bean>
</beans:property>
</beans:bean>
<beans:bean id="aducidAuthenticationProvider"
class="com.aducid.spring.security.AducidAuthenticationProvider">
<beans:property name="userDetailService" ref="aducidUserDetailService" />
<beans:property name="allowNullPrincipal" value="true"/>
<beans:property name="aimUrl" value="${aimUrl}/services/R4" />
<beans:property name="personalObjectId" value="ADUCID_USER" />
</beans:bean>
<beans:bean id="aducidUserDetailService"
class="com.aducid.common.services.DefaultAducidUserDetailService">
<beans:property name="authoritiesUserAttribute" value="aducidRole" />
</beans:bean>
</beans:beans>
